Confirmed working on OS X High Sierra
The proprietary CiscoVPN Mac client is somewhat buggy. It is possible to use the IPSec VPN software included with Mac OS X instead. This tutorial shows you how to migrate from CiscoVPNto the native OS X IPSec VPN by decrypting passwords saved in CiscoVPN PCF files.
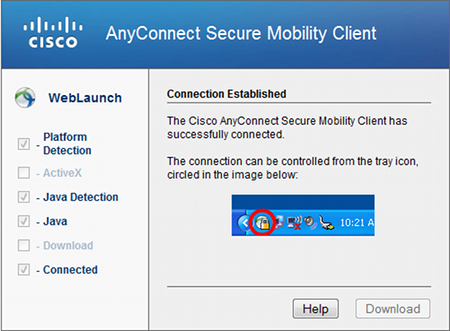
Click on the “Download Now” link for the “Cisco AnyConnect VPN Client Mac” and you will be prompted to log into the “NVPNSSO”. Click “Login.” 3. This will bring you to the NMU Login page where you sign in with your NMU credentials. The native OS X Cisco VPN adds these routes automatically and removes them when you disconnect. That's one of the things that differentiates the Cisco VPN client from the standard IPSec client. Let's take a look at what gateway is used when sending traffic to apple.com from within the Terminal application.
Please visit these guys if their offer interests you - they make this site possible.
The instructions below are tested on Mac OS 10.7.3 (Lion). Open System Preferences Network from Mac applications menu. Click the '+' button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu. A VPN client app 1/3 Cisco is a popular virtual private network (VPN) provider, and their VPN client is an app for taking advantage of these VPNs. With the client, you can establish a stable connection to remote systems with safety guaranteed. Follow the instructions below to download, install and connect the AnyConnect Secure Mobility Client on your Mac computer (OS X 10.9 or newer) to the new MSU VPN. Cisco Anyconnect Secure Mobility Client Mac Instructions Download: Cisco Anyconnect Vpn Client Free Download For Mac Os X. Go to https://www3.montana.edu/software.
Open up your System Prefrences and select 'Network'. Click on the little + button at the bottom of the window to create a new connection.
Pick 'VPN' for the Interface and set its type to 'Cisco IPSec'. It doesn't matter what you set as the service name.
Copy the 'Host' setting from CiscoVPN...
to the 'Server Address' setting in your System Prefrences' and enter your username under 'Account Name'. You probably don't want to enter your passwordunless you are OK with the system saving it.
On Mac OS X, PCF files are usually found in /private/etc/CiscoSystemsVPNClient/Profiles. Open up /Applications/Terminal and type the following:
You should get something like this:
Find that long list of letters and numbers after enc_GroupPwd= and copy it. Also make note of the GroupName - you'll need that in a bit as well.
Cisco Vpn Client Linux Mint 19
Paste that sequence of characters into the fancy schmancy decoder ring below and click 'Decode'. (pops up a new window)
Fancy Schmancy Decoder Ring
As an example, this should return 'letmein' as the password:
Thanks to HAL-9000 at evilscientists.de and Massar's work on cisco-decrypt.c for the magic here. A JavaScript implementation also exists here: https://github.com/artemkin/cisco-password-decoder.
Click 'Authentication Settings' back in the Network Prefrences screen. Enter the resulting decoded password into the 'Shared Secret' section of the new VPN connection and set the GroupName from above as well.
Click 'OK', make sure 'Show VPN status in menu bar' is checked and click 'Apply'.
At the top of your screen you should have a little VPN icon. Try connecting to your new VPN.
Cisco Vpn Client X64
If everything goes as planned, you should see your connection time counting up at the top of your screen.
How to get your VPN settings out of the built-in mac VPN client.
You don't need the Fancy Schmancy Decoder Ring to get your settings back out of the built-inMac VPN client. Just head over to the Keychain Access application (under Applications -> Utilities) and search for 'VPN'. Double-click your IPSec Shared Secret to open up the window. Clicking 'Show Password' will reveal the secret sauce after you authenticate.
If things seem to get hung-up and you are unable to reconnect your VPN without a reboot, Rick R mentions that you might try killing the 'racoon' process.
Racoon is an IPsec key management daemon and is part of the KAME IPsec tools. Kill it by running 'Activity Monitor' in the 'Utilities' folder, finding it in the process list and clicking 'Quit Process' at the upper left of the Activity Monitor window.
Look in your system.log by running the Console app for hints at what might be going wrong. Here's the system.log from aworking VPN setup / take down.
Disconnects
Dave Ma's VPN would disconnect after 45 minutes of uptime. Fotos Georgiadis on an Apple forum threadsuggested changing the IPSec proposal lifetime within racoon to 24 hours instead of 3600 seconds.(3600 seconds is 1 hour - who knows why people are seeing drops at 45 minutes)Here's how that is done.
Connect to the VPN (so OSX dynamically generates a racoon configuration file)
Open Terminal on Mac (Applications --> Utilities--> Terminal)
Copy the generated configuration file to /etc/racoon:
sudo cp /var/run/racoon/XXXXXX.conf /etc/racoon**where: XXXXXX is the name or ip address of your VPN server**
Edit the racoon configuration file with your favorite editor (pico):
sudo pico /etc/racoon/racoon.confAt the bottom of the racoon.conf file, comment out the line:
# include '/var/run/racoon/*.conf';(by added the '#' to the beginning of the line)
And instead include the copied file (which we will edit):
include '/etc/racoon/XXXXXX.conf';(don't forget to replace XXXXXX with the actual name of your file)
Edit the generated configuration file with your favorite editor (pico):
sudo pico /etc/racoon/XXXXXX.confDisable dead peer detection:
dpd_delay 0;Change proposal check to claim from obey:
proposal_check claim;Change the proposed lifetime in each proposal (24 hours instead of 3600 seconds):
lifetime time 24 hours;*note: make sure you change all the 'proposed lifetime' sections and not just one.
Disconnect and reconnect (this time racoon will use your custom configuration).
Now try using your VPN for more than 45 minutes and it shouldn't drop.
So does all your traffic flow through the VPN when you are connected or just traffic to the protected networks? Cisco VPN servers normally send out a list of routes to private networks so you don't end up sending all of your traffic through the VPN server. The reasoning behind this is why protect it if the traffic is destined for an insecure network anyway? The native OS X Cisco VPN adds these routes automatically and removes them when you disconnect. That's one of the things that differentiates the Cisco VPN client from the standard IPSec client. Let's take a look at what gateway is used when sending traffic to apple.com from within the Terminal application:
Notice the 'gateway' line there? Traffic to apple.com is going out 192.168.1.1 which is my normal Internet gatewayso it is skipping the VPN entirely.
Let's try an IP on a protected private network: (10.1.2.3)
In this case, the gateway is 172.131.25.12 which is a fake IP on the far end of the VPN which will eventually route traffic to 10.1.2.3. So when sending data to 10.1.2.3, I am going through the VPN and that traffic is encrypted.
So how does it know what gateway to use for different IPs? Let's take a look at the routing table:
I've lopped off a bunch of irrelevant lines but as you can see we have two 'default' routes. If a destination isn'texplicitly matched below, the traffic will flow through the first default route from the top. So in this case, ifthe destination isn't within 10.1/16 (which means 10.1.*.*) we will go through our default route of 192.168.1.1. Ifit is, we would go through 172.131.25.12 which is our VPN.
But what if you just wanted to send everything through your VPN connection? We could just delete the first default route and let everything go over the VPN, but this is presumably dangerous because the encrypted traffic probably uses the default route to get to the VPN server in the first place. Let's see:
Yep, it does. So if we are going to remove the default route to 192.168.1.1, we have to make sure we have an explicitroute below to the VPN server. (1.2.3.4) You will notice above that my Cisco VPN server adds this route automatically, but if yours isn't configured that way you can add it like this:
It is safe to try this if you already have the route because the command will just fail.
The next thing we are going to do is a little dangerous and remove all your network access. A reboot should be your weapon of last resort to get your networking back but you might also want to print these instructions out so you havethem. You have been warned!
Now let's do the dangerous bit and rip the first default route away:
Now let's check to see if we can still get to our VPN server:
Yep, looks good.
Now let's look at the wider Internet by seeing how we get to apple.com: (17.172.224.47 - we aren't using apple.com here because we don't want to depend on DNS working)
Whoops, something is wrong! That's because that first route there is a little deceptive. It isn't aroute to the IP of the gateway, just a route to the VPN tunnel device utun0. We'll need to say what IPto go to. Let's add a default route to the VPN's fakenet gateway address: (which we already have as the gateway in most other routes)
OK, let's see which way packets go to get to apple.com: (17.172.224.47)
Yep, looks like the right way.
Now let's try pinging google.com: (apple.com doesn't respond to pings)
Looks like it works. If it doesn't work, your VPN server likely doesn't allow general Internet access throughVPN connections. If this is the case, you are out of luck. Hopefully you know someone influential in the ITdepartment that can change this for you.
Because we removed the normal default route, when we shut down our VPN we'll be stuck without a default route.To add that back in after the VPN goes down, do this:
And we should be back to normal.
Ideally we do these things automatically when the VPN comes up. The easiest way to do this is to have yourVPN administrator set that up as a policy for you. Alternatively, you can create scripts that run on VPN startup.Create /etc/ppp/ip-up and add whatever lines you came up with above to that and mark that file as executablewith:
Similarly, /etc/ppp/ip-down will be run on VPN shutdown. Reverse your commands in that file and you shouldhave a completely automated setup.
Happy tunneling!
-Anders Brownworth
About Me:
Name:Anders Brownworth
Home: Cambridge, MA, USA
Work: Mobile application and GSM research at Bandwidth.
Play: Technology, World Traveler and Helicopter Pilot
Follow:
Contents
Introduction
Cisco Vpn Client X64 Download
This document briefly describes the possible error messages that appear during the installation of AnyConnect VPN client on Apple MAC machines and their corresponding resolutions.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
Cisco ASA Security Appliance that runs software version 8.x
Cisco IOS® Router that runs Cisco IOS Software Release 12.4(20)T
Cisco AnyConnect Client software version 2.x
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Error Messages
This section shows a list of error messages along with the solutions.
Package Corrupt Error Message
When AnyConnect 2.3 is launched from an Apple MAC machine, the Anyconnect Package corrupt or unavailable error message appears and eventually, the connection attempt fails.
Solution
This can be a problem with the absence of the MAC-related AnyConnect package on the flash of the router. Upload the suitable AnyConnect package for MAC in order to resolve this issue. Upload the corresponding AnyConnect package, which depends upon the MAC architecture. For MACs on the Intel processor, you need the i386 macos image and for MACs that run the Power PC processor (PPC) you need the powerpc macos image. These are example packages for your reference:
anyconnect-macosx-i386-2.5.3055-k9.pkg
anyconnect-macosx-powerpc-2.5.3055-k9.pkg
Split DNS Issues
When split DNS is enabled on an AnyConnect setup, it is found that all the DNS queries are sent in clear but not tunneled. This is a problem with only the Apple MAC machines and works fine with Windows machines.
Solution
This behavior is observed and filed in Cisco bug ID CSCtf03894 (registered customers only) . In order to resolve this issue, you can upgrade to the AnyConnect release 3.0.4235, which has the Split DNS Functionality Enhancement. As a workaround, you can also use the built-in IPSec VPN client supported by Apple, which does not have this issue.
SVC Error Message

The launch of AnyConnect from a Macbook Pro running OSX Leopard is not successful. The VPN gateway is ASA running 8.0.4. The connection fails and the SVC Message: 16/ERROR: Initialization failure (mem allocfailed, etc.) error message appears.
Solution
This can be a problem with the way the MAC machine attempts to connect to the ASA. First verify if any IPv6 adaptors are enabled on the MAC machine and check if MAC tries to contact ASA over the IPv6 network. If so, it fails as the IPv6 is not supported with AnyConnect. In order to resolve this, disable the IPv6 related services on the MAC machine and try to connect with an IPv4 address.

Web-based Installation Error Message when AnyConnect is Launched on MAC
There are intermittent issues with you launch the AnyConnect version 2.5 on the MAC with OSX 10.5.6. The web-based installation was unsuccessful error message appears. At that time, you are unable to download and install AnyConnect, and the browser used is Firefox. If you reboot the MAC machine, this fixes the issue temporarily, but intermittently, the issue happens again.
Solution
Verify if your VPN gateways are connected in Load-balancer mode. If it is connected, then there could be some DNS cache-related issues that cause improper DNS redirects. In order to resolve this issue, always try to map the DNS URL to connect to one specific VPN gateway only.
MAC OSX 10.6.3 is Unable to get to Internet
When you use the AnyConnect on a MAC machine, you can access the Internal Corporate network but you are unable to browse to the Internet. It neither works by FQDN nor by IP address. There is a proxy server in use for Internet traffic.
Solution
The issue can be due to the length of the PMTU. Verify the existing MTU size on the VPN gateway, for example, ASA and modify it to a lesser value. In this sample output, the mtu size is reduced to 1204 from existing 1400.
AnyConnect on MAC fails to launch to Cisco IOS Router
The attempt to launch AnyConnect in standalone mode to a Cisco IOS® Router running Cisco IOS Software Release 12.4(20)T is unsuccessful. The anyconnect internal error (state: not connected) error message appears.
Solution
Cisco IOS Software Release 12.4(20)T supports AnyConnect on MAC in standalone mode without any problem. In order to resolve this, try to use the complete URL when you connect to the Cisco IOS head-end device. This is a sample URL:
If this issue persists, contact Cisco TAC (registered customers only) for further troubleshooting.
Note: You need to have valid Cisco user credentials to contact Cisco TAC.
Wireless CSSC for an Apple MAC
Currently, the NAM module on the AnyConnect 3.0 product replaces the Cisco Secure Services Client (CSSC). Refer to Network Access Manager (Replacement for CSSC) for more information. There is no current plan to enable NAM to support MAC OSX platform.
Unable to Upgrade Firefox while AnyConnect is Installed on MAC
This error message appears when you upgrade Firefox on Apple machine version 10.6:
On machines that use softtokens, this error message appears:
It is observed that these MAC machines have AnyConnect version 2.5 installed. The current version of Firefox is 3.6.13.
Solution
This behavior has been tested and filed in Cisco bug ID CSCtn93915 (registered customers only) . As a workaround, you can try any of these described options.
Uninstall AnyConnect, upgrade Firefox and then install AnyConnect again.
Uninstall the current version of firefox then install the new version. All other upgrades after this should work fine.
Web-based Installation of AnyConnect Hangs
The authentication phase works fine but the VPN system hangs at the Using Sun Java for installation phase.
Cisco Vpn Client Export Profile
Solution
The issue could be with the Java and Web applet settings on the machine. Sometimes, Java gets stuck when you use the web launch with MAC machine. Refer to Cisco bug ID CSCtq86368 (registered customers only) for more information. In order to resolve this issue, follow the below steps.
Uninstall AnyConnect.
Open Java preferences.
Change to run applets in their own process.
Drag the 32 bit Java on top.
If this does not help, upgrade the AnyConnect client to the latest available release.
Unable to Launch AnyConnect on MAC
You are unable to launch AnyConnect on the MAC machine due to certain incompatible software. What are other options to use this MAC machine as a remote access VPN client?
Cisco Vpn Client Mac Download Free
Solution
Refer to What options do I have for providing remote access to Mac users? for more information. Refer to IPSec VPN client for Apple MAC for more information and complete details.
Unable to Download the MAC AnyConnect Package
There are issues when you download the AnyConnect for MAC software from Cisco.com.
Download Cisco Ssl Vpn Client
Solution
Cisco Vpn Client Ios Configuration
Open the Cisco AnyConnect VPN Client home page and click on Download Software (registered customers only) on the right hand side of the web page. Choose the required software package and download with valid Cisco user credentials.
Related Information
